tldr - powered by Generative AI
A new variant of the banking trojan BBTok is targeting users in Brazil and Mexico, replicating the interfaces of over 40 banks to trick victims into entering their credentials. The malware uses various techniques to evade detection and carries out banking activities only upon command from its control server. The threat actors behind BBTok are likely operating out of Brazil, and the malware poses a significant danger to organizations and individuals in the region.
- BBTok is a banking trojan targeting users in Brazil and Mexico, replicating the interfaces of over 40 banks to deceive victims.
- The malware uses evasion techniques such as living-off-the-land binaries (LOLBins) and geofencing checks to avoid detection.
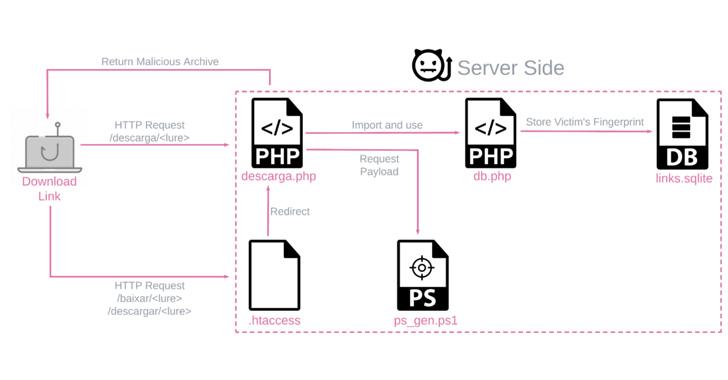
- BBTok establishes connections with a remote server to receive commands and simulate security verification pages of banks.
- The malware aims to harvest credential and authentication information for account takeovers.
- The operators of BBTok are cautious, executing banking activities only upon direct command from the control server.
- The malware has improved its obfuscation and targeting since 2020, expanding beyond Mexican banks.
- The presence of Spanish and Portuguese language in the source code suggests the attackers' origin in Brazil.
- BBTok has infected over 150 users based on an SQLite database found in the server hosting the payload generation component.
- The Israeli cybersecurity company Check Point has also reported a large-scale phishing campaign targeting companies in Colombia, aiming to deploy the Remcos RAT.
- Remcos RAT grants attackers full control over infected computers and can lead to data theft, follow-up infections, and account takeover.
Tags:
BBTok
banking trojan
Brazil
Mexico
evasion techniques