-
Categories:
2024-05-07
tldr - powered by Generative AI
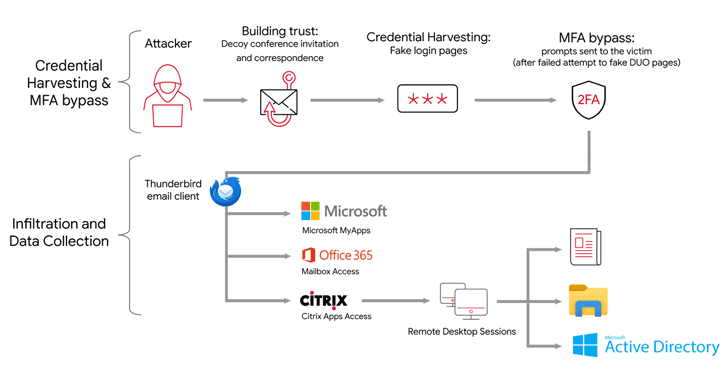
APT42 hackers are using social engineering tactics to infiltrate target networks and cloud environments, posing as journalists and event organizers to gain trust and harvest credentials.
- APT42 uses social engineering schemes to gain initial access to victim networks by posing as journalists and event organizers.
- The hackers harvest credentials and bypass multi-factor authentication to access cloud environments.
- APT42 relies on publicly available tools, exfiltrates data to a OneDrive account, and uses VPN and anonymized infrastructure to cover its tracks.
- Custom backdoors like NICECURL and TAMECAT are used as jumping points to deploy additional malware or execute commands.
- APT42 remains focused on intelligence collection despite other Iran-nexus actors adapting to disruptive activities.
Tags:
APT42
social engineering
Hacking
cloud security