tldr - powered by Generative AI
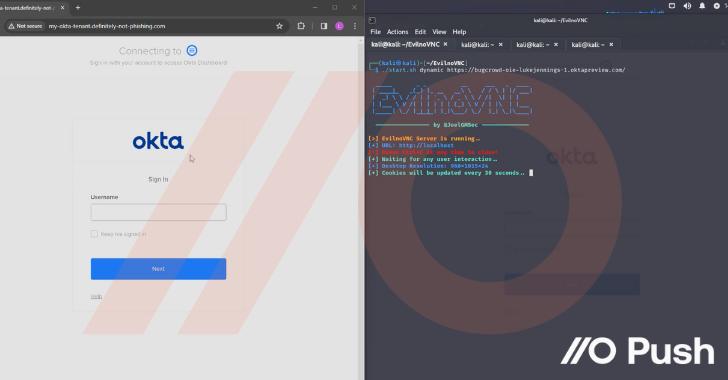
Cloud identities are the new perimeter in cybersecurity, and organizations need to be aware of the various attack techniques that can target businesses in the cloud.
- Cloud identities are now the primary focus for cybersecurity defenses.
- Attack techniques such as AiTM phishing, IM phishing, SAMLjacking, Oktajacking, and shadow workflows can bypass traditional security measures.
- Push Security has released a matrix of SaaS attack techniques and blog posts to educate on these threats.
- Organizations must be vigilant and implement strategies to protect against these cloud-based attacks.
Tags:
cloud security
identity attacks
phishing techniques